Academy of Information Security and Internet Intelligence
0+
Students on paid programs since 2022
0+
Users have passed our free courses
Professional solutions for multi -accounting
0+
Customers with us since 2024
0+
High-quality IP addresses for proxy
Training specialists, who make the world safer
5,0/ 5



Free books on anonymity and security online
They will teach you to remain anonymous on the network, be inaccessible to cyber espionage, and securely protect your data.



Excellent4.8 out of 5Trustpilot
Professional solutions for multi-accounting
Advanced solutions for multi -accounting
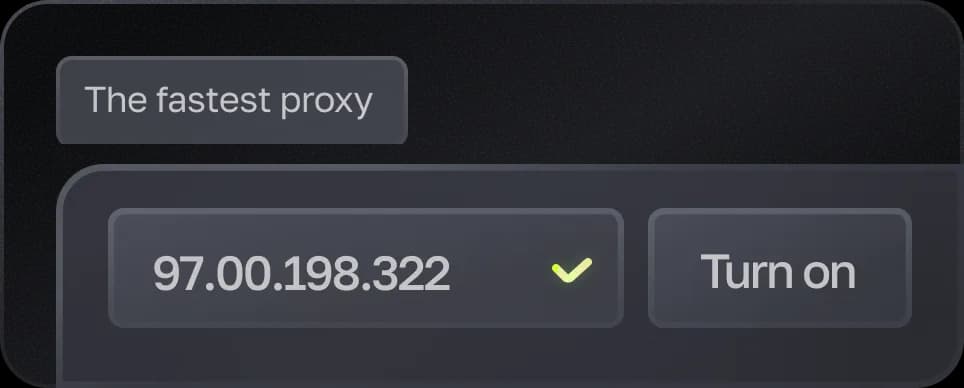
Mobile proxies LTE/5G
Proksi based on real mobile devices is a reliable solution for working with services that require a high level of trust. A manual IP shift is available
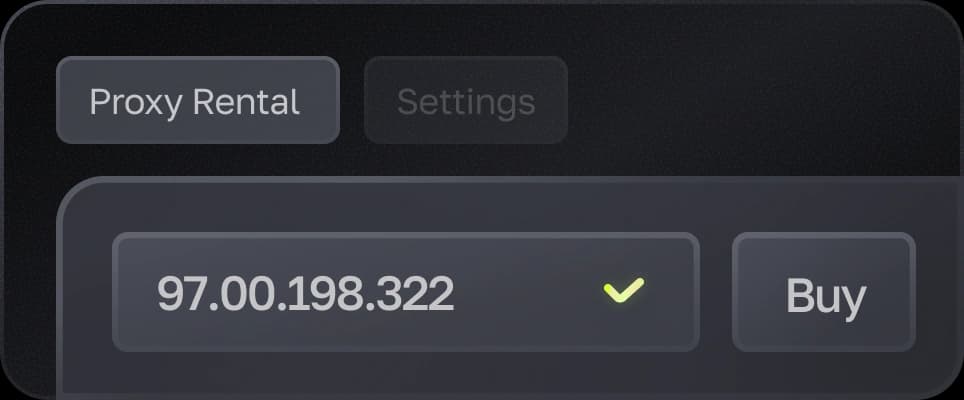
Residential proxies
Proxy from real Internet providers with wide geographical coverage (static IP or rotation)
3674 6251 8824 1266
Exp.Date: 25/12
Virtual bank cards
Rent a bank card in 1 minute and pay for purchases around the world without restrictions
3674 6251 8824 1266
Exp.Date: 25/12
We accept all types of payments
Excellent support service
More than 11 years of successful work
Cryptocurrencies that will suit you



Get the freshest educational content in our media
Telegram channel
@cyberyozh_official60K subscribers
YouTube channel
@CyberYozh
65K subscribers